 The Indian banking and financial services market is undergoing a major transformation. In the payment market, cash, credit, and debit cards are giving way to digital alternatives. Though fruitful to the financial sector, the rising inclination towards digital interface is also increasingly facing threat from cyber breaches, writes Rashi Aditi Ghosh from Elets News Network (ENN).
The Indian banking and financial services market is undergoing a major transformation. In the payment market, cash, credit, and debit cards are giving way to digital alternatives. Though fruitful to the financial sector, the rising inclination towards digital interface is also increasingly facing threat from cyber breaches, writes Rashi Aditi Ghosh from Elets News Network (ENN).
The Banking, Financial Services and Insurance (BFSI) sector is changing from a traditional manual model to an automated processdriven business model. With the adoption of digital technology, the consumer behaviour is also evolving. Traditional players are facing new competitors in direct banking as well as mobile banking segments.
However, the menace of cyber attacks on financial services companies is increasingly getting diverse, thus unpredictable. The frequency of these threats is rising and perhaps is here to stay.
While talking about the cyber threat vulnerability of financial institutions, Bharat Berlia, Chief Information Officer, Indus Net Technologies, said: “Technology is evolving at a rapid pace and such advancements within the banking and financial sectors are likely to introduce new vulnerabilities and complexities.”
“Adoption of alternate channels like online payments, mobile, cloud, and social media technologies further increases the chances of exploitation. Sometimes due to pressure of achieving faster goals or cost reductions, there are compromises made in the overall IT infrastructure. As we move more and more towards the open-ended technologies, financial institutions will have to work on stringent controls, depending on trusted vendors.”
Explaining technologies role in dealing with cyber attacks, Harshil Doshi, Strategic Security Solutions Consultant – India, Forcepoint says, “We are in the age of data breaches. With cyber security intrusions seeming to take place almost every day, cyber security technology becomes an indispensable tool in preventing breaches, data theft, meeting compliances and enable better decision making for organisations. While technology plays a central role in containing threats, it must be noted that people and processes are equally important. People, Process and Technology form a holistic security strategy for organisations in addressing constantly evolving cyber security challenges and regulatory requirements. e.g. Insider attacks are becoming more prevalent than external attacks in modern times. In highly sanitised environments, technology is required to identify anomalies in user behaviour to protect network and stop loss of critical data. UEBA (User and Entity Behavior Analytics) and DLP (Data Leakage Prevention) are being widely used in high security environments.”
Data Breach Turning Expensive
A report by IBM-Ponemon Institute shows that cyber breaches are getting expensive for India. The per capita cost of a compromised record went up by over 75 per cent in the past five years. The cost has swelled from Rs 2,106 in 2012 to Rs 3,704 this year, according to a report by the institute.
Rising Concern of Cyber Attacks in India
|
In a cyber attack of unprecedented scale, safety of over 32 lakh debit cards was compromised this October, the culprit being a malware. It was reportedly the biggest data breach in the Indian banking history.
India was ranked third worldwide, next only to the US and China, as a target for cyber criminals in 2015, according to a 2016 report by software security firm Symantec Corp.
According to the India Risk Survey-2016 conducted by Pinkerton and FICCI, the information and cyber insecurity has been listed as the second biggest threat to businesses in India for two consecutive years.
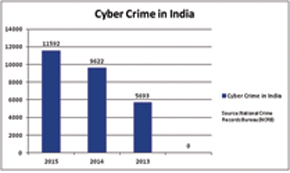
As per the data maintained by National Crime Record Bureau (NCRB), a total of 5,693, 9,622 and 11,592 cybercrime cases were registered during 2013, 2014 and 2015, respectively, showing a rise of 69 per cent during 2013 to 2014 and 20 per cent during 2014 to 2015.
|
The Evolving Cyber Threat Landscape
To achieve growth, cost optimisation and innovation, financial service companies are everyday adopting businesses and high-end technologies. But this quest is also exposing them to heightened levels of cyber risks. These innovations have most likely introduced new vulnerabilities and complexities into the financial services technology ecosystem.
Account Takeovers: Cyber criminals have demonstrated their ability to exploit online financial and market systems that interface with Internet, such as the Automated Clearing House (ACH) systems, card payments, and market trades.
Payment Systems: Fraudulent monetary transfers and counterfeiting of stored value cards are the most common result of exploits against financial institutions, payment processors, and merchants.
According to the India Risk Survey-2016, the information and cyber insecurity has been listed as the second biggest threat to businesses in India.
ATM Skimming: ATM skimming is also a prevalent global cyber-crime. A criminal affixes a skimmer to the outside or inside of an ATM to collect card numbers and personal identification number (PIN) codes.
Point of Sale Terminals: Point of Sale (POS) terminals have been a primary target for cyber criminals engaging in credit card fraud and have resulted in the compromise of millions of credit and debit cards.
Mobile Banking Exploitation: As more mobile devices have been introduced into personal, business, or government networks, they have been increasingly targeted for stealing. Cyber criminals have successfully demonstrated man-in-the-middle attacks against mobile phones using malwares.
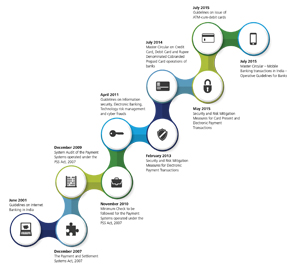
Increased Regulatory Requirements Banking in India is governed through various legal and regulatory requirements issued by the Government of India and the banking regulator – Reserve Bank of India (RBI).
RBI on regular intervals issues various circulars and guidelines on various aspects of banking.
The RBI guidelines on information security, electronic banking, technology risk management and cyber frauds, issued in April 2011, define the fundamental information security requirements which all banks need to follow.
In addition to the above guidelines, there are multiple regulatory requirements related to internet banking, payment systems, mobile banking, IT outsourcing, etc which may be applicable to a particular bank, depending on the context of the organisation and the nature of its operations in India.
Talking on the importance of regulations in context of cyber security, Doshi, Strategic Security Solutions Consultant – India, Forcepoint says, “The cyber security regulations make it compulsory for the organisations to protect their systems and information from cyber attacks. Government and industry regulators including banking regulators have taken note of increased role of IT and therefore consider cyber security as an essential component of the economy. Secondly, cyber security is important for the protection of critical infrastructure systems. So, regulations act as minimum deterrent against cyber threats that should be in place at any point in time for organisations. However, in view of changing technology landscape and rising internal attacks, the regulations must be reviewed periodically to include threats coming from emerging landscape.”
Speaking on the policy issues related to cyber security, Ilias Chantzos, Senior Director Government Affairs EMEA-APJ, Symantec, said, “I think if someone looks at it from a covered policy landscape, we see challenges associated technology and policy-making. This is the reason why there has been a shift change to cloud. To meet the challenges, there is a need to deploy more of Internet of things (IOT) devices as all the threat is emerging due to explosion and proliferation of data.”
“Like other countries across the globe, India too is facing a lot of security threat but as per our observation, India has been extremely successful in terms of digital transformation,” he added.
Why Should Financial Services Consider Cyber Security?
Financial service firms should consider raising their level of preparedness and evolve into a new cyber risk management paradigm that strives to achieve three fundamental qualities:
- It is important to be secured against known threats through risk-driven investment. This can be ensured by adapting a secured foundation, preventive controls, and policies.
- Security can be assured by improving the ability to detect emerging threats and anomalous patterns amid the highly complex and data-saturated environment.
- Ability to form a sturdy organisation that can recover from attacks as quickly as possible and minimise both direct and indirect damages.
India was ranked third worldwide, next only to the US and China, as a target for cyber criminals in 2015, according to a 2016 report by software security firm Symantec Corp.
Mechanism To Rule Out Cyber Attacks
Actionable threat intelligence – derived from a wide range of sources and well-defined governance processes, which instill cyber risk awareness, accountability and effective continuous adaptation can be critical fuel in driving this paradigm shift. For many firms, what are currently called IT risk management programmes can evolve into executive-driven cyber risk management programmes that are an integral part of strategic business planning.
Multi-pronged Approach to Managing Cyber Risks – Financial services firms have traditionally focused their investments on becoming secure. However, this approach is no longer adequate in the face of the rapidly changing threat landscape. Put simply, financial services companies should consider building cyber risk management programmes to achieve three essential capabilities: the ability to be secure, vigilant and resilient.
Enhancing Security through a “defence-in-depth” Strategy – A good understanding of known threats and controls, industry standards and regulations can guide financial services firms to secure their systems through the design and implementation of preventative, risk-intelligent controls.
A report by IBM-Ponemon Institute shows that cyber breaches are getting expensive for India. The per capita cost of a compromised record went up by over 75 per cent in the past five years.
Based on leading practices, financial services firms can build a “defence-in-depth” approach to address known and emerging threats. This involves a number of mutually-reinforcing security layers both to provide redundancy and potentially slowdown the progression of attacks-in-progress, if not prevent them. Such slowing down can work in the defendant’s favour by providing adequate time to secure their digital assets and mount effective counter-strategies.
 Enhancing vigilance through effective early detection and signaling systems – Early detection through the enhancement of programmes to detect both the emerging threats and the attacker’s moves can be an essential step towards containing and mitigating losses. Incident detection that incorporates sophisticated and adaptive signaling and reporting systems, can automate the correlation and analysis of large amounts of IT and business data, as well as various threat indicators, on an enterprise-wide basis.
Enhancing vigilance through effective early detection and signaling systems – Early detection through the enhancement of programmes to detect both the emerging threats and the attacker’s moves can be an essential step towards containing and mitigating losses. Incident detection that incorporates sophisticated and adaptive signaling and reporting systems, can automate the correlation and analysis of large amounts of IT and business data, as well as various threat indicators, on an enterprise-wide basis.
Financial services companies’ monitoring systems should work 24×7, with adequate support for efficient incident handling and remediation processes.
Enhancing resilience through simulated testing and crisis management processes — Resilience may be more critical as destructive attack capabilities gain steam. Financial services firms have traditionally planned for resilience against physical attacks and natural disasters; cyber resilience can be treated in much the same way. Financial services companies should consider their overall cyber resilience capabilities across several dimensions:
First, systems and processes can be designed and tested to withstand stresses for extended periods. This can include assessing critical online applications for their level of dependencies on the cyber ecosystem so as to determine vulnerabilities.
Second, financial services firms can implement good playbooks to help triage attacks and rapidly restore operations with minimal service disruption.
Finally, robust crisis management processes can be built with participation from various functions including business, IT, communications, public affairs and other areas within the organisation.
Explaining about the Cyber security perspective and ways to deal with it, Berlia from Indus Net Technologies, said, “Our security experts get involved at the initial stages of the project and design an architecture which secures data, people, facilities, process and technology. The idea is to identify, prioritize and manage risk relative to its potential impact on mission-critical operations maintaining organizational agility. Our solutions usually provide real-time visibility into processes, systems, data and equipment.”
Elets The Banking and Finance Post Magazine has carved out a niche for itself in the crowded market with exclusive & unique content. Get in-depth insights on trend-setting innovations & transformation in the BFSI sector. Best offers for Print + Digital issues! Subscribe here➔ www.eletsonline.com/subscription/















