Introduction
The financial services industry, particularly the banking industry, by its far-reaching and widespread operations in the country, has been pivotal for the improvement of the nation’s economy. The country’s economy is judged by how far the banking industry is faring at a particular point in time. Also, every other establishment in the country requires a safe and reliable financial service as a facilitator to perform their (business) activities smoothly. The importance of banking services being a critical infrastructure in the value chain makes it vital for banks to ensure the security and integrity of their financial services.
The alarming trend in which cybersecurity-related incidents are reported targeting organisations belonging to all sectors, the financial services sector ranking most targeted, shows the daily lurking troubles the industry faces.
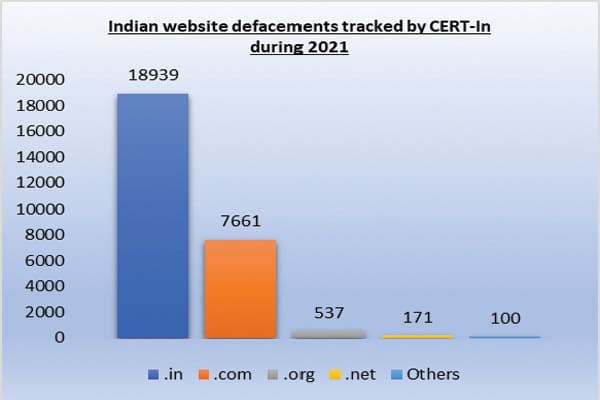
As per the Annual Report 2021 of the Indian Computer Emergency Response Team (CERT-In), it handled a total of 14,02,809 incidents during the year. The type of incidents handled was Website Intrusion & Malware Propagation, Malicious Code, Phishing, Distributed Denial of Service attacks, Website Defacements, Unauthorised Network Scanning/ Probing activities, Ransomware attacks, Data Breach and Vulnerable Services. A total of 618 security alerts, 52 advisories, and 390 Vulnerability Notes were issued during the year 2021. The number of reported incidents, alerts, and advisories issued shows the growing trend in cyber-attacks and the negative advantage taken for the exposed vulnerabilities.
With the increase in digitisation in all banking aspects, including customer onboarding, transfers, and payments, collections, remittances, contactless payments, digital wallets, etc., the threats and attacks have also become sophisticated and prevalent.
What is the worry?
The evolving threats faced by the banking sector include phishing/ vishing scams, ransomware attacks, card data theft, ATM jackpotting and others such as denial of service (DoS) attacks that are not only affecting the services offered but also the image of the institutions in the eyes of the general public. Overall, the threats being faced by the banking sector are immense and sophisticated.
These constant and ingenious threats posed by cybercriminals have kept the banking sector on their toes and compelled them to understand the importance of such attacks and how to constantly be vigilant to protect their business operations. The banks are making themselves equipped to understand and analyse patterns in such occurrences to prevent or minimise future threats.
The various risks to be considered both internally and externally by the banks may be in the form of
- Infrastructure
- Employees
- Partners
- Vendors
- Customers
Each of these players must be considered and evaluated for the cyber risks posed
and a suitable preventive mechanism has to be worked out for all the use cases. The banks need to upgrade their cybersecurity operations to tackle the growing volume and scale of these cyber threats comprising the evolving landscape of organised cybercriminals, state-sponsored hackers, hacktivists and insiders. The motive of these players is to steal data, identity, and information and use the same for extortion, espionage activities or bring disruption to operations.
Security infrastructure in banks is faced with the huge challenge of tackling many alerts related to threats and taking measures to mitigate them daily. The response to any threat must be immediate along with plugging the vulnerability identified to leave no room for the attackers to take advantage. The banks need to proactively monitor and counter all relevant threats with all the possible means at their disposal. Though the transition from legacy systems and tools to modern infrastructure is complete in banks, they require a holistic approach to the security risks to counter them across all types of infrastructures.
The solution
All banks today have their state-of-the- art Security Operation Centres (SOC) comprising various teams that deal with threat monitoring, incident response, vulnerability fiXing, and other related cyber risk management procedures. These centres operate using data and tools from different sets often lacking proper collaboration and relevance, thus decreasing the overall efficiency of risk management.
The solution is to build the next- generation Security Operation (SecOps) capabilities that help centralise, integrate and streamline the operations to maximise risk identification and accelerate response time. The challenge for banks is that the technology infrastructure is spread across different environments physically and logically which has to be taken into consideration for the solution being envisaged. The technologies like SOAR – Security Orchestration, Automation and Response (refers to a collection of software solutions and tools that allow organisations to streamline security operations in three key areas: threat and vulnerability management, incident response, and security operations automation) can
be leveraged to drive security strategies for banking organisations to be highly responsive and scalable.
Threat Intelligence
In addition to the sophisticated security tools and infrastructure, the security strategies should also comprise threat intelligence to keep pace with highly ingenious and agile threats to make smarter decisions. So, what is threat intelligence? Wikipedia says, “Cyber threat intelligence is knowledge, skills and experience-based information concerning the occurrence and assessment of both cyber and physical threats and threat actors that are
intended to help mitigate potential attacks and harmful events occurring in cyberspace.”
Banks need to start utilising threat intelligence to improve their cyber security operations and be proactive in dealing with cyber-attack incidents. The security teams at banks need to learn to prioritise and execute the detection and response mechanisms to ensure maintaining focus on the critical threats and how to minimise their consequences.
The cyberattack lifecycle normally has the following stages.
1. Reconnaissance: The stage where the cybercriminals do a recce of the target to gather information and intelligence to plan their attack. These threat actors collect the required information through various means, like websites and emails to employees to have an idea of the security aspects followed.
2. Weaponisation and Delivery: The second stage is to weaponise the vulnerabilities found in the earlier stage. The attack will be delivered through methods like phishing, smishing, malicious attachments, etc.
3. Exploitation: Once the malware is delivered and deployed in the system, code, or network of the intended target, this stage successfully gets the first foothold into any organisation.
4. Installation: The stage provides a connection to the target’s system or network to enable the malware to compromise the identified area.
5. Command and Control: Like its nomenclature, this stage is where the adversaries start to effectively take control of any application, system or network of the target. Sensitive data and information are also gathered during this stage.
Also Read | BFSI sector adapting a dynamic cybersecurity stance
6. Actions: The final stage is where the cybercriminals take steps to achieve their goals like gaining publicity, defacing websites, and claiming ransom, thus causing embarrassment and image loss for the affected organisation.
To avoid cyberattacks in their early stage(s), the lifecycle described above should the understood to put in place strategic, technical, tactical, and operational threat intelligence in security practices and processes, thereby minimising the threat impact. While collecting data/ information from diverse sources may be easy, deploying threat intelligence to improve mechanisms to detect and respond is more difficult. Also, these actions need to be included in the organisation’s overall cybersecurity strategy. To achieve this, banks need to leverage automating most of the actions required and providing last-mile threat intelligence to all the stakeholders quickly and effectively across the organiation.
The sharing of threat intelligence also plays a vital role in the cybersecurity strategy, not only within the organisation but also outside with other industry players, regulatory agencies, law enforcement agencies, and communities. This will help to coordinate
and strategise collectively through a proper information-sharing mechanism. Also,
a learning mechanism can be developed to improve defences against cyberattacks
through this network of information sharing.
Conclusion
The risks of cyber-attacks are growing by the second and the banking sector, dealing in financial services is more prone to such attacks. Banks, being custodians of public money, must be more responsible for preventing such attacks and ensuring security. Keeping this in mind, the sector must be over-enthused to investing in cybersecurity comprising of technologies, processes, and people to monitor, detect and avert any casualties.
Views expressed by: Prasanna Babu M R, Research Officer, SBI, Hyderabad.
Elets The Banking and Finance Post Magazine has carved out a niche for itself in the crowded market with exclusive & unique content. Get in-depth insights on trend-setting innovations & transformation in the BFSI sector. Best offers for Print + Digital issues! Subscribe here➔ www.eletsonline.com/subscription/